Pegasus spyware can now be detected on an iPhone using a free tool without requiring coding skills. Geneva, Switzerland-based DigiDNA has updated its iOS device manager iMazing with a spyware detection feature that can be used to detect Pegasus. The company has designed the feature using Amnesty’s Mobile Verification Toolkit (MVT) as a reference. The tool can be installed on a Mac or a Windows PC to let you discover whether your iPhone was exploited using Pegasus. The spyware was allegedly used by governments in various parts of the world including India to snoop on activists and journalists.
The spyware detection feature is available as a part of iMazing 2.14. It uses the same list of indicators of compromise (IOCs) that Amnesty International’s Security Lab compiled to help people detect Pegasus infection on their devices. Some privacy experts praised the new tool for how user friendly it is, compared to the earlier methods.
Although chances are quite low that you would be affected by the spyware if you aren’t famous anyone can still use iMazing on your computer to detect whether Pegasus has infected their iPhone. You can download the tool for free on your Mac or Windows PC from the iMazing website.
![]()
Pegasus spyware detection is possible using iMazing
DigiDNA CEO Gregorio Zanon said in a blog post that the spyware detection feature is built on MVT’s methodology that Amnesty International released as an open-source development last month — shortly after the news revealing the military-grade spyware attack shocked the masses. However, unlike the original toolkit that requires command line knowledge and some coding skills, you can use iMazing even if you don’t have those technical expertises.
It is important to note that iMazing’s offering is specifically designed for devices based on iOS and is not available for Android phones. It also doesn’t have support for analysing file system dumps from jailbroken devices.
How to detect Pegasus spyware on an iPhone using iMazing
To begin with the steps on how you can detect the existence of Pegasus spyware on your iPhone, you firstly need to have the latest version of iMazing installed on your Mac or Windows machine. The spyware detection feature is available even for the people using iMazing under its free trial. However, the software is available as a freemium and requires a licensing fee to unlock all its features.
-
Once you’ve installed the iMazing 2.14 or later on your computer, click on Continue Trial when prompted for the first time.
-
You can now connect your iPhone to your computer using a Lightning cable to detect Pegasus spyware.
-
Now, you will see key options available under the free trial on the right hand. Scroll down through those options and choose Detect Spyware.
-
A new window will now open to guide you through the process. Hit the Next button to begin with the spyware detection tool.
-
The iMazing app will now ask you to download the latest Structured Threat Information Expression (STIX) files from the server.
-
After the download completes, the app will ask you to create a local backup of your iPhone data for analysis. It will also ask you to enable Backup Encryption. This will password-protect your backup. You should store the password for future reference.
-
iMazing will now start backing up your data. You don’t need to do anything manually at your end as the app will automate the backup task.
-
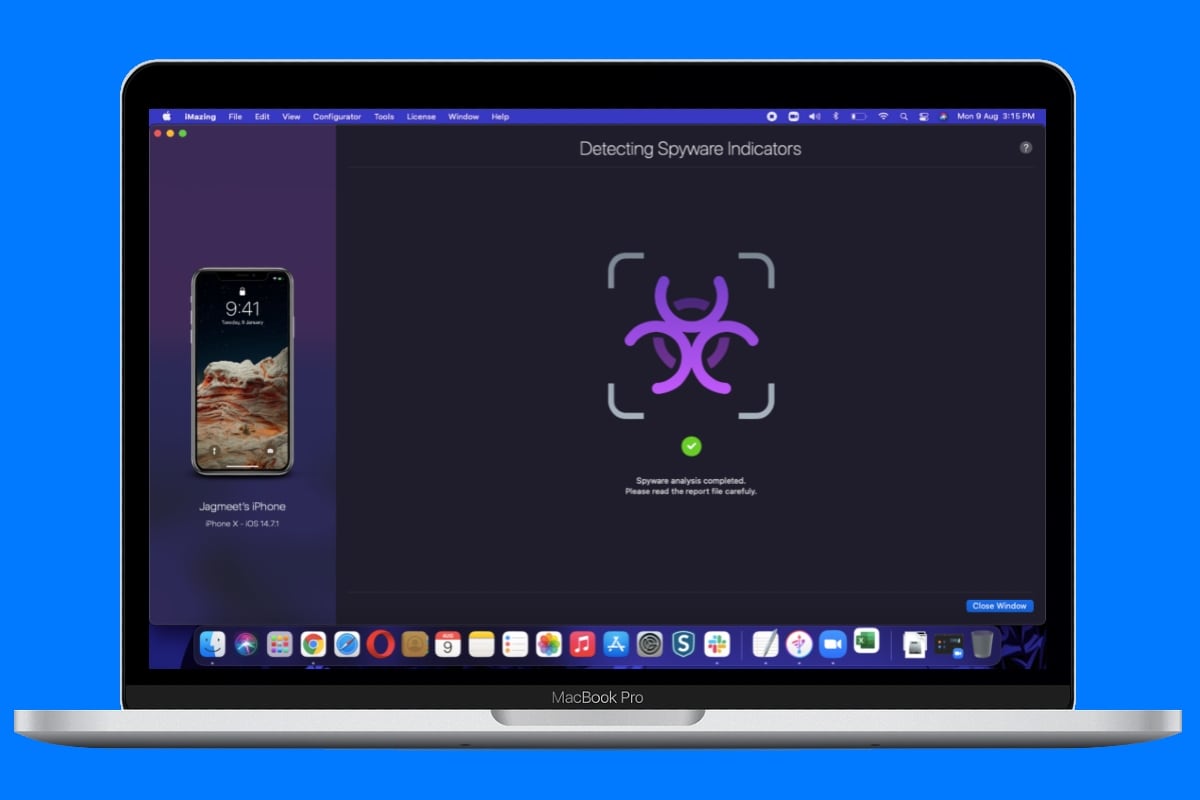
Once the backup process gets over, iMazing will decrypt the data and analyse files for the Pegasus spyware.
-
It will then show you the outcome — whether the spyware was planted to infect your device. You will see the number of warnings and the total number of logs. The app will also let you open the entire report in Excel to look at the warnings.
We noticed that it takes about half an hour’s time for iMazing to have the backup ready, though the analysis part doesn’t take more than five to 10 minutes. In our testing, we found two warnings but those were just due to some parse errors.
DigiDNA recommends users to reach out to its customer support team to let it do further analysis. This will help avoid false positive cases. The company also suggests that if you have got a positive report and you or your family members are active in a “politically sensitive context”, you should immediately remove your SIM card and turn your iPhone off.